Space is no longer the exclusive domain of engineering behemoths
with a “monumental mission” mindset, as a new ecosystem of technology
innovators democratizes extra-terrestrial commerce.
For fifty
years, space innovation meant scaling Apollo-era technologies into ever larger,
more durable satellites parked above their terrestrial clients in
geo-synchronous orbit. Exotic space-ready parts, militarized defenses, and
layered redundancies ballooned into multi-billion dollar systems designed to
last 40 years or more beyond their conceptions. Only vast organizations with
thousands of aerospace engineers could participate.
By the turn
of the century, it didn’t matter that geo-synchronous orbit resembled a stadium
parking lot on Super Bowl Sunday. The internet had upended and bankrupted the
commercial space industry, whose expensive, decades-old satellites could no
longer compete with terrestrial means of moving information. And when a financial
crisis gripped the global economy one decade ago, constricting the government
budgets that funded most space exploration, NASA’s cancellation of its flagship
programs seemed to ring the death knell for our colonization of the cosmos.
The space
community was dispirited; no one expected an imminent, explosive emergence of a
new entrepreneurial ecosystem that now promises unprecedented opportunities in
space and vanishing barriers to extra-terrestrial commerce. The prospect of
colonizing the Moon, Mars and beyond now seems likely and even palpable.
The New Mindset
Space colonization
began in 1957 with the launch of Sputnik, followed by the monumental Apollo
program that landed humans on the Moon. Both Sputnik and Apollo had to develop
their entire missions and supply chains from scratch: rocket engines,
spacecraft, avionics software, space suits, ground stations, mission control software,
and more.
This monolithic
approach dominated space missions until recently. In 2010, Brooklynite Luke
Geissbuhler and his son Max heralded a new model for space exploration when
their amateur weather balloon ferried an iPhone 19 miles above the surface of
the Earth, capturing beautiful space images
as expensive satellites do. Luke and Max’s fun experiment exploited the low
cost of mass-produced cell phones, whose batteries, antennas, radios,
accelerometers and cameras constitute the most common components of commercial
satellites.
Meanwhile, students at Cal Poly and
Stanford were using those same cell phone components to assemble what they
called CubeSats – 10x10x10 cm buses designed to cheaply ferry their science
experiments on Low Earth Orbit. (In LOE, where satellites naturally de-orbit within
five years due to drag from atmospheric particles, they don’t need exotic
radiation-proof parts.) Standard modules for DIY cubesats can now be procured
on hobbyist sites as easily as buying a book on Amazon.
Like the DARPA engineers who coded the
internet protocol, these students hadn’t appreciated the impact of their invention.
Cubesats sparked a realization that true scalability comes not from bigger
satellites, but many cheap small ones, and suddenly five accumulated decades of
Moore’s Law turned the space industry upside down. Venture-backed startups like
Planet Labs
and Skybox (now merged) developed constellations of micro-satellites to image
the Earth far faster than enormous, lumbering incumbents. Other ventures like SpaceX and OneWeb are deploying
massive constellations to serve the planet with internet and IoT
communications. The Silicon Valley teams behind all these constellations
naturally focus on software-driven designs with commodity hardware, enabling
satellite operators to quickly launch new apps as we do on our smartphones. The
largest general purpose cubesat constellation – roughly 60 “Lemurs” operated by
Spire Global –
already monitor ships, planes and weather.
The new mindset that space is best
colonized by smaller, cheaper, faster computers not only admits entrepreneurial
engineering teams – it favors them. Hundreds of other startups are now
exploiting the 100X cost savings of microsat constellations to colonize space.
A New Ecosystem
The microsat revolution demands a new
ecosystem to support the operators of these constellations. By far the most
important and difficult input to procure is launch, since all mature rocket
programs were designed long ago to carry enormous, expensive payloads to
Geosynchronous Orbit with 5-10 years of advanced notice; new players like
Virgin Orbit, Firefly and Rocket Lab promise cheap and frequent carriage to Low
Earth Orbit. Next-gen operators also need ground stations, mission control
software, satellite tracking, data analysis, life support systems, human
habitats, robotic mining systems, space WiFi, and more. Sat and rocket
manufacturers in turn need specialized software, subsystems, amplifiers, phased
array antennas, miniaturized propulsion, materials, extensible solar panels,
and batteries. And innovators in additive manufacturing like Velo3D enable SpaceX
and Rocket Lab to design and 3D print far more efficient engines.
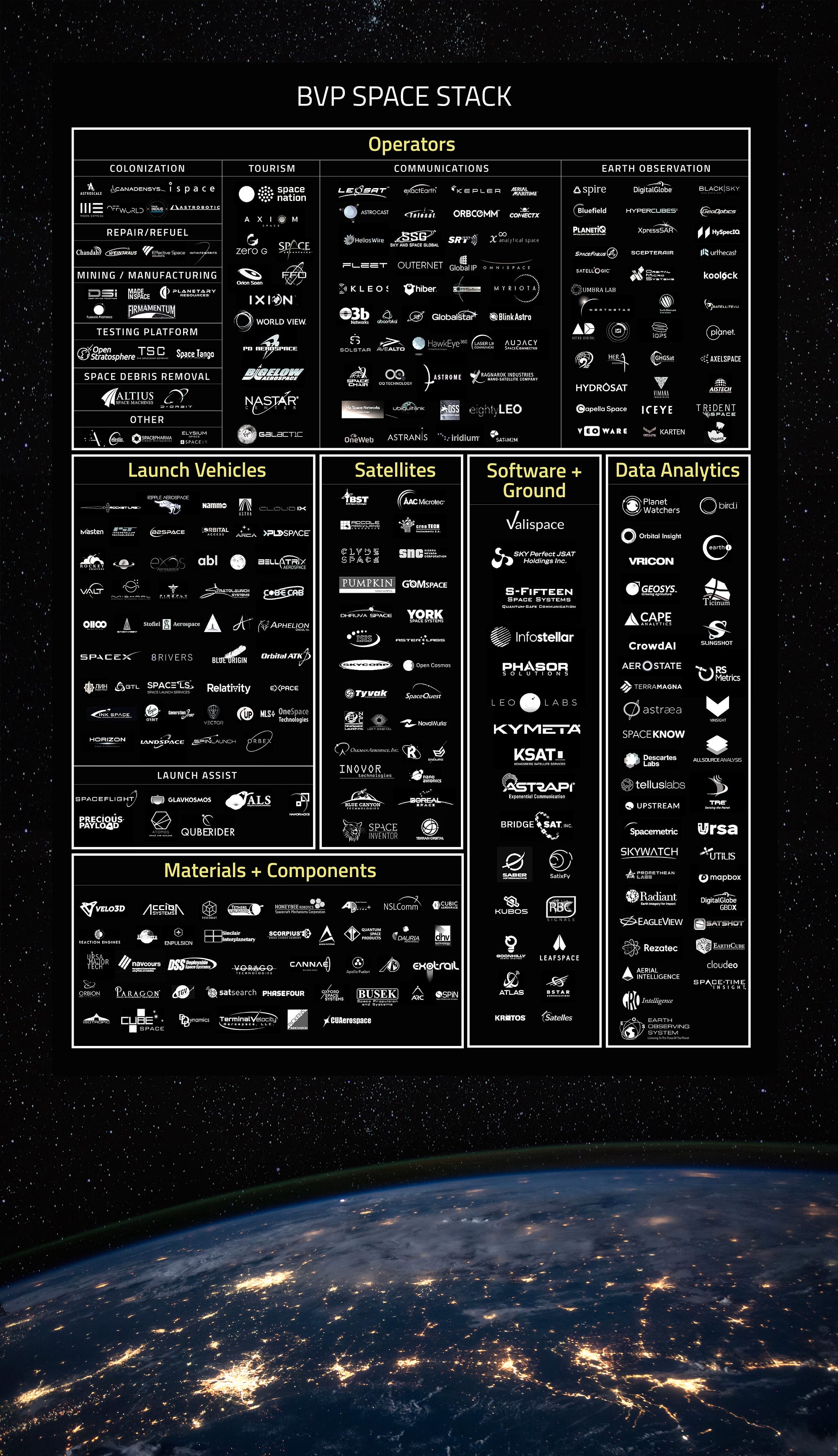
Space companies now assemble cheaper,
better, faster constellations by mixing and matching off-the-shelf elements
from this emerging fragmented ecosystem. This new Space Stack (see illustration)
promises a virtuous cycle of innovation, diversity and growth akin to the explosion
of datacom startups sparked in the 1980s when the OSI 7-Layer Internetworking
similarly disrupted an oligopoly of proprietary networks from IBM, Digital HP
and Sun.
Atop the space stack sit the microsat
operators who create value for people on Earth. They are extraterrestrial
mining companies, agricultural intelligence businesses, pharma manufacturers,
internet service providers, weather forecasters, marine tracking companies, and
new ones every month. As the space stack
grows, these companies look less like scientific research labs, and more like their
terrestrial competitors.
In other words, space is open for
business. Entrepreneurs are flocking to the final frontier, where Moore’s Law
has unleashed massive, enduring opportunities. This is how Humanity will
colonize Low Earth Orbit, the Moon, the asteroids, Mars and beyond – through the
emergence of a distributed, commercial ecosystem infinitely more powerful than
any single company or government.